Matching Resources and Business Risk
Gaining visibility and responding to attacks across the entire enterprise infrastructure (endpoints, servers, applications, SaaS, cloud, users, etc.) is a very tall order in today’s cybersecurity environment. To meet this challenge, enterprises are forced to create complex security stacks consisting of SIEM, UEBA, SOAR, EDR, NDR, TIP, and other tools. For many enterprises, SIEM is the primary tool for aggregating and analyzing data from the infrastructure. Nearly half of enterprises report that they are not satisfied with their SIEMs. However, all enterprises will be quick to point out the amount of capital, time, and resources they have poured into standing up and maintaining their SIEMs. Open XDR is emerging as a new approach addressing the challenge of gaining visibility and responding to attacks across the entire enterprise infrastructure. This article will look at how Open XDR and SIEM measure up as security solutions.
Defining Open XDR
Gartner defines XDR, or eXtended Detection and Response, as “a unified security incident detection and response platform that automatically collects and correlates data from multiple proprietary security components.” This definition, dating back to 2020, does not capture Open XDR as an emerging category of XDR that collects and correlates data from all existing security components, not just proprietary or single-vendor ones. So, Open XDR is defined the same as Gartner’s XDR definition except that it ends with “all existing security components, delivered via an open architecture.” The Open vs. Native XDR difference is discussed in detail in another article. In this article, we focus on Open XDR as it compares to SIEM. So Open XDR has the following technical requirements to fulfill the promise of the above definition:
- Deployability – Cloud-native microservice architecture for scalability, availability, and deployment flexibility
- Data Fusion – Centralize, normalize and enrich data across the entire attack surface, including network, cloud, endpoints, applications, and identity.
- Detection – Built-in automated detections through Machine Learning
- Correlation – High-fidelity correlated detections across multiple security tools
- Intelligent Response – One-click or automated response from the same platform.
Sound similar to SIEM plus a little SOAR? That’s because it is. However, there are significant architectural differences that allow Open XDR to deliver on many of the promises of SIEMs where SIEMs have fallen short.
Defining SIEM
Gartner defines SIEM, or Security Information and Event Management, as technology that “supports threat detection, compliance and security incident management through the collection and analysis (both near real-time and historical) of security events, as well as a wide variety of other event and contextual data sources.” This definition is notably similar to the definition of XDR. Architecture is where the most significant differences lie, but purely definitionally, a SIEM was named after its primary purpose – to manage information and events. XDR was also named after its primary purpose – to detect and respond. This may seem like a minor point, but this difference in business purposes drives the architectural approach and is why SIEMs are so capital-intensive in today’s security environment.
Architectures Compared
This comparison focuses only on the differences. Several technical similarities include long-term storage, open integrations with security tools, cloud-nativity, and efficient search and threat-hunting.
However, Open XDR has five key architectural differences from SIEMs:
1. Data is forced into a normalized and enriched state. This is done before the data are stored in a data lake.
2. AI automatically drives detections and correlation of alerts in Open XDR, not human-written rules as with SIEMs.
3. Incidents are produced from correlated alerts. A single response on the same platform is orchestrated, compared to a SIEM, which sends alerts to a different SOAR platform that then performs downstream correlation and response.
4. Many tools required for security operations are unified, such as Big Data Lake, UEBA, SOAR, TIP, NDR, or EDR on one platform. In contrast, many SIEMs only include a Big Data Lake, forcing SIEM users to combine many complex tools manually.
Differences 1 and 2 go hand in hand. The data problem must be solved to build and maintain meaningful AI in any industry. In security, that means data must be centralized, normalized, and enriched to reduce data complexity. If data is modeled differently at each platform deployment, it will be an impossible problem to maintain AI models. XDR forces data to be modeled the same way across each deployment before data lands into a Data Lake; data is only available in its normalized and enriched state. SIEM either provides this as optional functionality or does not provide this feature at all; in the optional case, normalization and enrichment are treated as a post-processing step on the already stored raw data.
In summary, on technical differences 1 and 2, Open XDR forces normalization and enrichment on data, so it can build meaningful AI that correlates events and alerts together. For the same reasons, SIEM architecture cannot produce an AI engine of the same fidelity because of its treatment of data. SIEMs will leverage AI, but it will be challenging to scale.
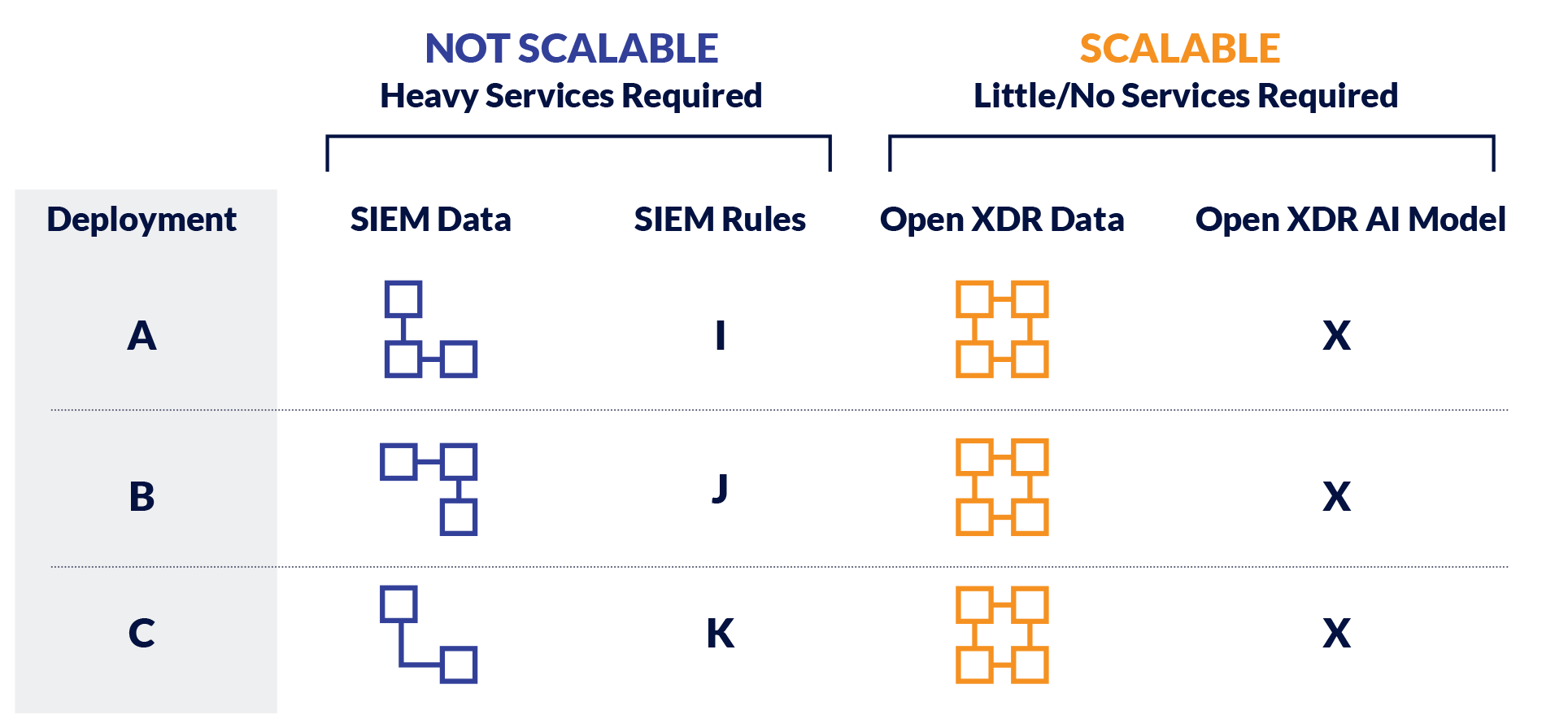
Technical difference 3 comes down to an Open XDR performing correlation and response in the same platform. A higher-order construct of an incident (multiple related alerts) is automatically produced in an Open XDR platform, which is responded to holistically. A SIEM must pass alerts to a SOAR, which must correlate alerts with rules without the deep context of everything happening in the environment. Open XDR produces a response just like a SIEM and SOAR does. However, the response fidelity is much greater with XDR because it is orchestrated from the same platform performing detections and AI-driven correlations, where all the data is available.
The final technical difference is centered around building and maintaining the overall security stack. Open XDR was designed to unify all critical tools for security operations such that they can be orchestrated from one platform. Many SIEMs offer long lists of plugins and deep levels of customization, but that puts the onus on the users to build and configure their system.
For the enterprise, these technical differences influence the capital, time, and resources it takes to run a security platform. SIEMs are open-ended technologies, so they will be expensive to operate. Open XDR platforms are security prescriptive technologies, and therefore enterprises will be much more efficient when employing them.
Finally, while not strictly technical differences, two areas where SIEMs have focused much more are on heavy compliance-related storage and use of the same platform for IT Operations; XDR is designed for the outcome of detection and response. It can still meet compliance requirements, but it was not designed for that from the start. IT Operations in the same platform is something only SIEM can claim, as Open XDR is strictly focused on security.
Navigating The Collision Course of XDR And SIEM
XDR is on a collision course with SIEM and SOAR, as noted by Forrester2. Enterprises need to approach both technology categories with their long-term business outcomes and available resources in mind. Are high fidelity, automated detection, and response out of the box more critical? Is the capability of response from the same platform by the same team necessary to reduce the attack dwelling time? Is the team short-staffed and/or needs lots of training to run the tool? These are the key questions enterprises must bring to the table when defining their security stack strategy and deciding whether XDR or SIEM is right for them.
What About NG-SIEMs?
“Next Gen” anything signals something better, not different. NG-SIEMs are better than SIEMs in the hypothetical sense. Open XDR is different from both. NG-SIEMs brought considerable advancements in many areas where legacy SIEMs were not keeping up with the demands of today’s security environment. Notable improvements are:
- Use of Big Data technologies (no more
- SIEM constantly falling over)
- Some User and Entity Behavior Analysis (UEBA) through various algorithms
- UI/UX improvements to key workflows
- like Threat-Hunting
- Native or open integration with SOARs
- Data modeling plugins.
NG-SIEMs certainly close the capability gap between Open XDR and SIEM, but the architectural differences remain the same.
Some Vendors Say They Offer A SIEM and An XDR Platform – What Gives?
There are many similarities between SIEM and Open XDR, as noted above. The technical differences are nuanced but significantly affect the business value and capital required to operate. There are two claims vendors make if they use both SIEM and Open XDR to describe their products.
The first claim vendors may make is that they may use “SIEM Capabilities” to refer to their Open XDR platform having all the critical capabilities of a SIEM – open collection, storage, search, reporting, cloud-native. They say this to describe how Open XDR can be deployed in an enterprise security stack, specifically to replace an existing SIEM.
The second claim vendors may make is that their platform is both a SIEM and an Open XDR platform. This is a confusing point likely to ensure that the vendor does not miss out on potential category marketing and can sell a product to customers regardless of whether they are looking for SIEM or Open XDR. As discussed above, however, SIEM and Open XDR are different, so the same product cannot be both.
[1] 2017 Ponemon SIEM Report
[2] https://www.forrester.com/report/Adapt+Or+Die+XDR+Is+On+A+Collision+Course+With+SIEM+And+SOAR/-/E-RES165775
We gathered select industry articles that may be of interest to you in your search for the best Managed Security Service options.
Managed Security Services
The complexity of securing today’s enterprise has become even more daunting, businesses with large and small IT staffs are looking to Managed Security Service Providers (MSSPs) to shift risk from their IT departments into the hands of dedicated security professionals.
Memo from the White House: What We Urge You To Do To Protect Against The Threat Of Ransomware
Read the White House memo urging corporate executives and business leaders to take immediate cybersecurity steps and lists the five best practices for safeguarding against ransomware attacks.
New Ransomware Strategies for 2021
How to detect breaches early through lateral movement. Short discussion followed by a 5 minute demo
Global Threat Landscape Report
The latest Global Threat Landscape Report represents the collective intelligence of FortiGuard Labs. Its data is drawn from Fortinet’s vast array of sensors collecting billions of threat events observed around the world and processed using one of the world’s most advanced AI systems during the second half of 2020.
MSSP Adoption: Managed Security Services Demand Surges in UK
UK businesses will increasingly outsource cybersecurity to managed security services providers (MSSPs), new NTT research findings & forecasts suggest. by Dan Kobialka • Oct 30, 2017 A lack of cybersecurity skills and a need for advanced technology is leading many UK businesses to partner with managed security services providers (MSSPs), according to a report from security, risk and compliance services company NTT Security.Key findings from the NTT Security “Risk: Value 2017” report,…
What does stolen data cost [per second]
Trading in intellectual property and personal data is so widespread that someone invented a calculator that can estimate the potential harm to your own business.Nearly 5 million data records are lost or stolen worldwide every single day, according to the Breach Level Index. That’s a staggering 58 records every second. High-profile data breaches hit the headlines with worrying frequency. Just last year there were notable incidents at Equifax, Verizon, and Kmart, to name just the three biggest…
The Benefits Of Managed Security Services For Online Businesses
Managed Security Service Providers (MSSPs) are third party providers of expert security services. They work by offering security services either in-house or remotely, overseeing everything from setting up security processes to ensuring smooth day-to-day running. Online businesses need to be on top of their security to prevent data hacks and breaches and using an MSSP creates an easy and reliable way to do so. There are many reasons why every online business, from e-commerce to retail, can be…
Evolution of Managed Security Services in the Future
The need to protect delicate information and sensitive data as well as thwart organized cyber attacks has driven industries across several verticals—including banking, manufacturing, healthcare, and retail—to employ Managed Security Services (MSS). MSS are third-party security service providers that remotely monitor and manage the network infrastructure of such organizations. While most organizations today manage IT security in-house, a rising trend among IT professions is to partner with an …
Do Not Underestimate the Challenge of Securing SD-WAN
Historically, the branch office of an organization was the red-headed stepchild of the network. Locally cached data tended to be out of date and connections to the central data center were often slow and unreliable. This was fine when interactions with customers and databases were slow, and the number of devices connected to the branch network was limited. But digital transformation has changed all of that.Today, transactions, workflows, applications, and data requests at the branch need to…
5G Security Transformation: Why Businesses Need to Prepare Now
New 5G networks will offer faster speeds, lower latency and more reliable connections, launching a new era of wireless networking and connected solutions. As a result, it is projected that the number of 5G users will grow to more than a billion by 2023. Many of these customers will take advantage of 5G speeds to deploy new Internet of Things and connected devices that employ edge-based computing to process huge volumes of data. To address this explosive rate of growth and innovation, business…
How to Select a Managed Security Service Provider (MSSP)
Credit: ID 17575170 © Hannu Viitanen | Dreamstime.com During a recent trip to the Gartner Security and Risk Summit in Sydney, I attended a session on how to select a Managed Security Service Provider (MSSP), which had some really good points on what customers need to understand when evaluating an MSSP. Traditionally, Managed Security Service Providers (MSSPs) have offered security services such as managed anti-virus, managed firewall, and web filtering which consist of conducting tas…
5 Reasons to Purchase Cybersecurity From a VAR
The digital business model requires organizations to adopt a new approach to securing data and networks. At the same time, technology and networks are evolving, making security more complex.One of the biggest challenges is the sheer number of security products and vendors inside an organization. According to our technology partner Fortinet, Some larger financial enterprises; for example, use products from as many as 40 or more vendors to secure their networks.All these products — firewa…
Xiologix Recognized as a 2020 Top Provider!
“CRN’s Managed Service Provider 500 list recognizes the top technology providers and consultants whose forward-thinking approach to providing managed services is changing the landscape of the IT channel.” Access the full list here. Xiologix is proud to have made this list with the additional distinction of being named as a “Pioneer 250”. Our networks are expanding and evolving faster than ever. The saying, “don’t fix what isn’t broken” doesn’t work in today’s technical environments. It is…
XDR Explained In 300 Words
Most XDR definitions are tedious & long. To give MSSPs clarity, Stellar Cyber VP Brian Stoner explains XDR security in 300 words. by Stellar Cyber • Jun 2, 2021 XDR is the rising star of new acronyms, but everyone wants you to read a 1,000+ word blog to understand its value. Let’s try to do it in about 300 words.Author: Brian Stoner, VP of service providers, Stellar CyberX means to expand DR’s – detection and response systems – to cover your entire attack surface, not just a portio…



